Boosted by GenAI in the world of technology, code development has been vastly improved with efficiency without necessarily compromising originality. Nevertheless, behind all the wonders of automated coding stands a silent but important concern - the oversight of weak links within GenAI-created code. The Promise of GenAI-Generated Code GenAI's learning tool, which can imitate...
Blog
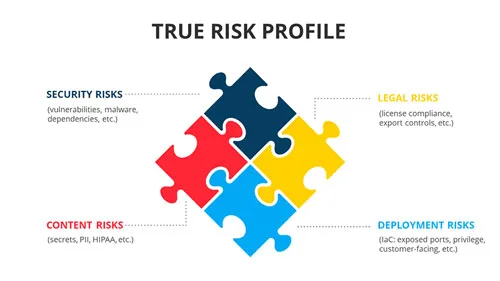
Container security is the practice of correlating all inherent security risks in conjunction with the context of how the container is deployed and used. The risks can include vulnerabilities, dependencies, secrets, malware, IaC, licenses, and more. By adding the context about how each container is deployed, exposure to hackers, and how it is used, and...
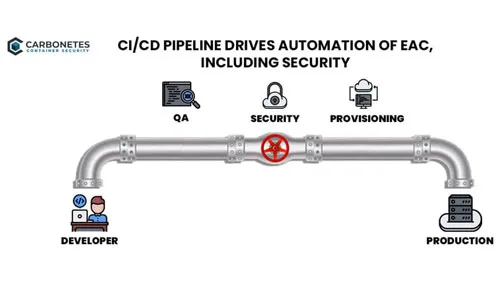
Modern security tools provide a variety of implementation options including full-function clients, APIs and CI/CD plugins. What is the best option for you? The answer to that depends on your role and how you will use the tools. Are you doing software development, security, or management? For software developers, integrating security inside their CI/CD tools...

Securing a container involves analyzing for a variety of potential risks over a variety of components inside, or associated with, the container. There are two approaches: comprehensive analysis—analyzing for all risks—or assembling a collection of specialty analyzers. Another way of phrasing this decision is whether the whole (comprehensive) is greater than the sum of the...
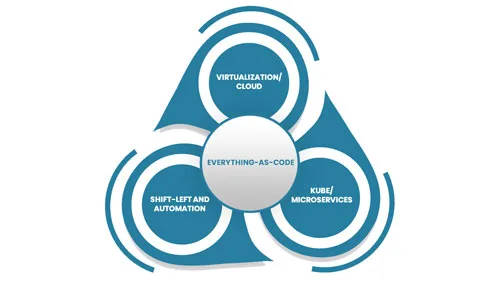
Video Overview of Everything-as-Code (6:27 minutes) Everything-as-Code (EaC) is the future of IT; the benefits are simply overwhelming. EaC is the next logical step of DevOps; the merger of development and operations. Under the DevOps model, developers took responsibility for running their code. EaC gives developers responsibility to define everything, especially the underlying infrastructure that...

With the growth of technology, AI and cybersecurity have engendered questions about threats that may come from the use of artificial intelligence. In trying to get into details on this complex dance, we must analyze and determine whether AI threatens cybersecurity or functions as a beneficial ally. The Dual Nature of AI in Cybersecurity...

The cloud-native revolution has transformed how we develop and deploy applications. Infrastructure as code (IaC) and containerization with technologies like Docker and Kubernetes have become foundational elements for building and managing modern software systems.
