Boosted by GenAI in the world of technology, code development has been vastly improved with efficiency without necessarily compromising originality. Nevertheless, behind all the wonders of automated coding stands a silent but important concern - the oversight of weak links within GenAI-created code. The Promise of GenAI-Generated Code GenAI's learning tool, which can imitate...
Blog
Keeping your containers secure could mean the difference between a thriving business and a total data breach. Here are five of the best practices for container security. Containers have revolutionized the way applications are deployed and run. They offer many benefits over traditional virtualization technologies, such as great portability, performance, and density. However, containers also...

Infrastructure as Code (IaC) is not as simple as some other security risks because IaC is not automatically right or wrong. Vulnerabilities are easy, if you have a vulnerability, it is bad and you want to remediate it, no questions asked. IaC may not follow a best practice, but it may still be appropriate or...
What is Infrastructure as Code (IaC)? You can think of IaC as a universal configuration file that tells your infrastructure platform—which can include the cloud, Kubernetes, Function-as-a-Service (FaaS), storage, and other services—how to handle a running piece of code. IaC describes rights, scaling constraints, resources, and more. Prior to IaC, you had to configure each...
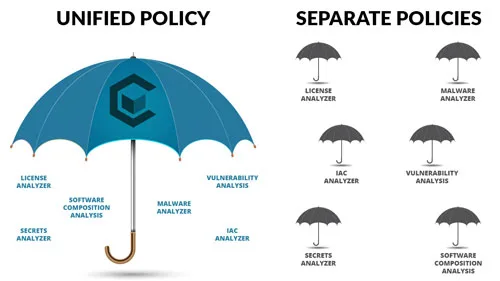
Security policies are a critical component of your security solution and selecting the right security policy is critical to secure development. This article looks at the different types and provides insight into what to look for in a security policy to balance security and development efficiency at scale. Security policies encapsulate a company’s requirements for...

With the growth of technology, AI and cybersecurity have engendered questions about threats that may come from the use of artificial intelligence. In trying to get into details on this complex dance, we must analyze and determine whether AI threatens cybersecurity or functions as a beneficial ally. The Dual Nature of AI in Cybersecurity...

The cloud-native revolution has transformed how we develop and deploy applications. Infrastructure as code (IaC) and containerization with technologies like Docker and Kubernetes have become foundational elements for building and managing modern software systems.
