Find Malware in Your Dependencies
Finding and eliminating malware early in the Software Development LifeCycle (SDLC) saves time and money while keeping your software secure and compliant. Early detection safeguards your reputation, promotes better coding practices, and ensures a more trustworthy product.
At Carbonetes we provide malware detection to protect your dependencies:

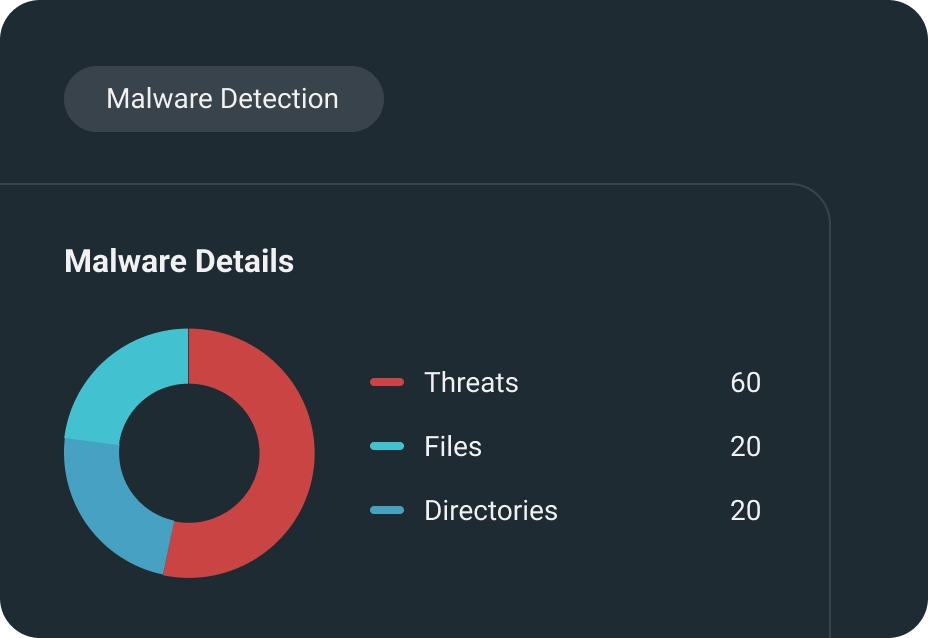
Identify & Eliminates
Identify & Eliminate malicious software to protect the integrity of your Container Images and File Systems.

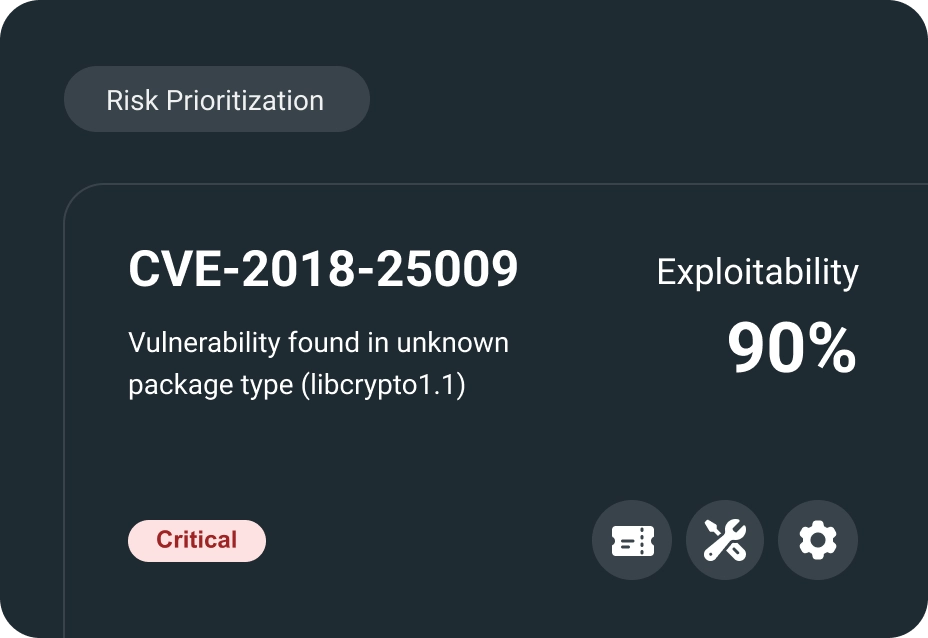
Integration with Jira
For easy creation of tasks and prioritization, simplifies your workflow and ensures timely resolution of security issues.

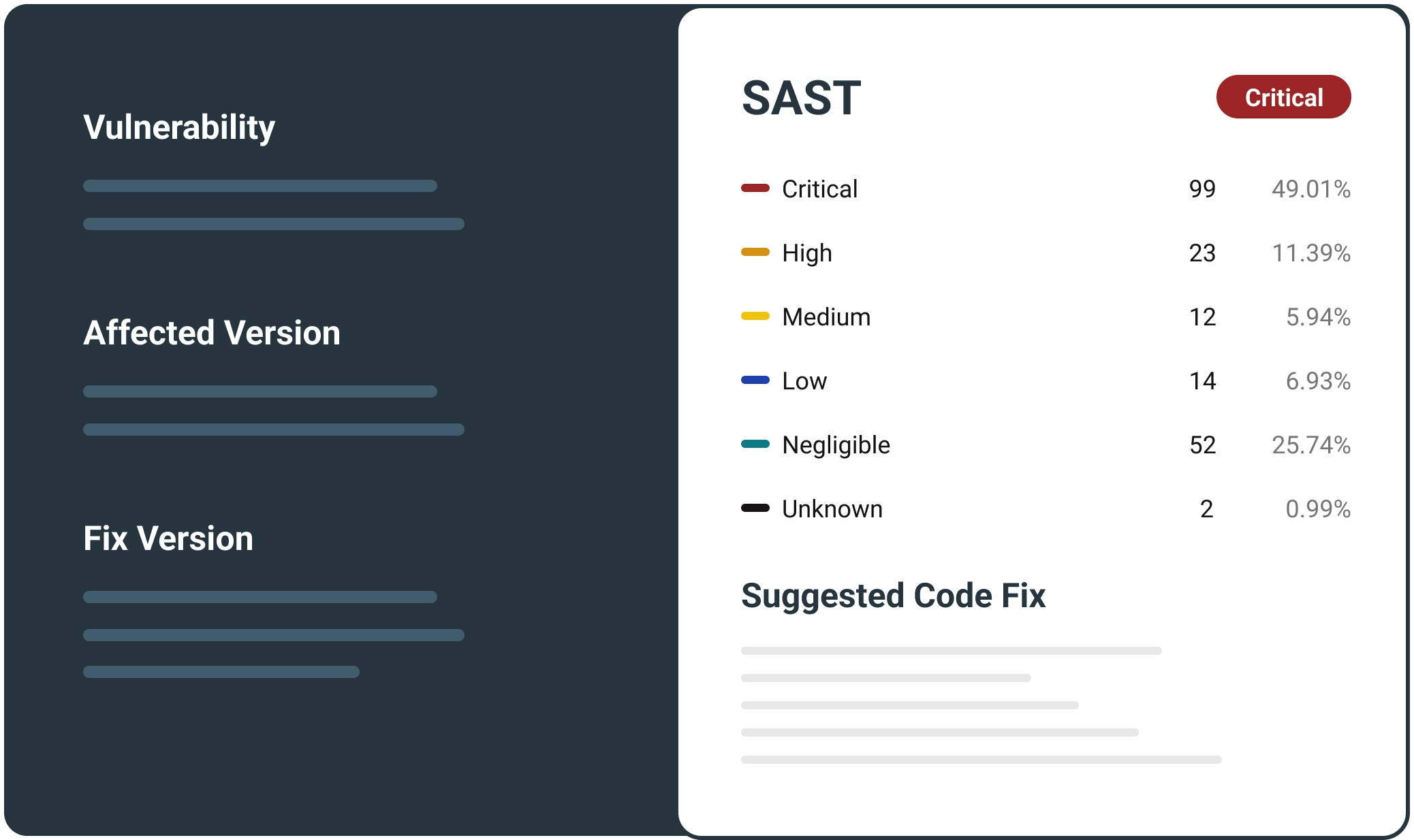
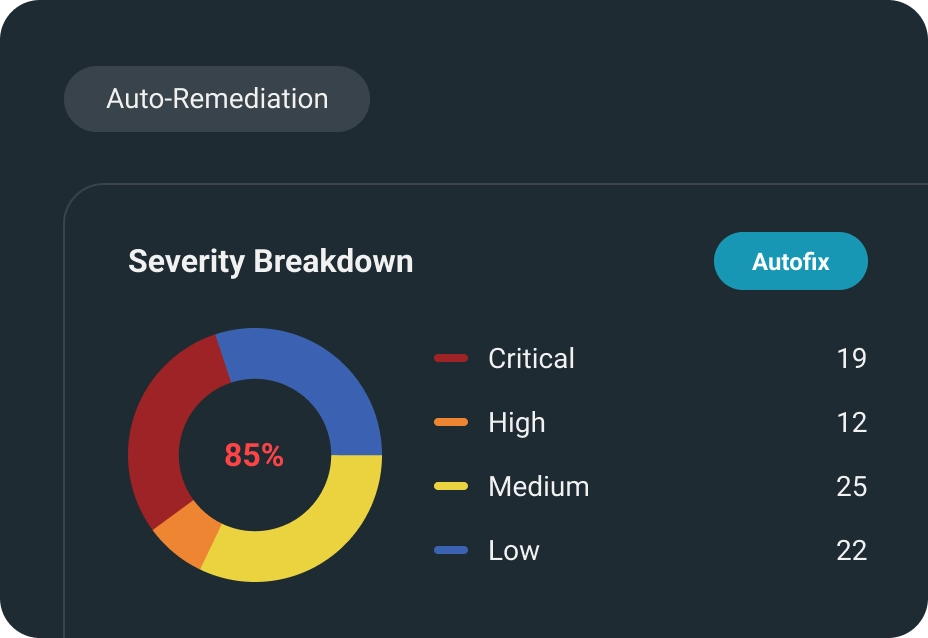
Policy Evaluation
Evaluates your security risks and compares them to your security policies based on NIST, CIS, or custom policies you can build, test and automate, using our policy builder.