Silicon Valley, CA
Houston, TX
Seattle, WA
(650) 683-0394
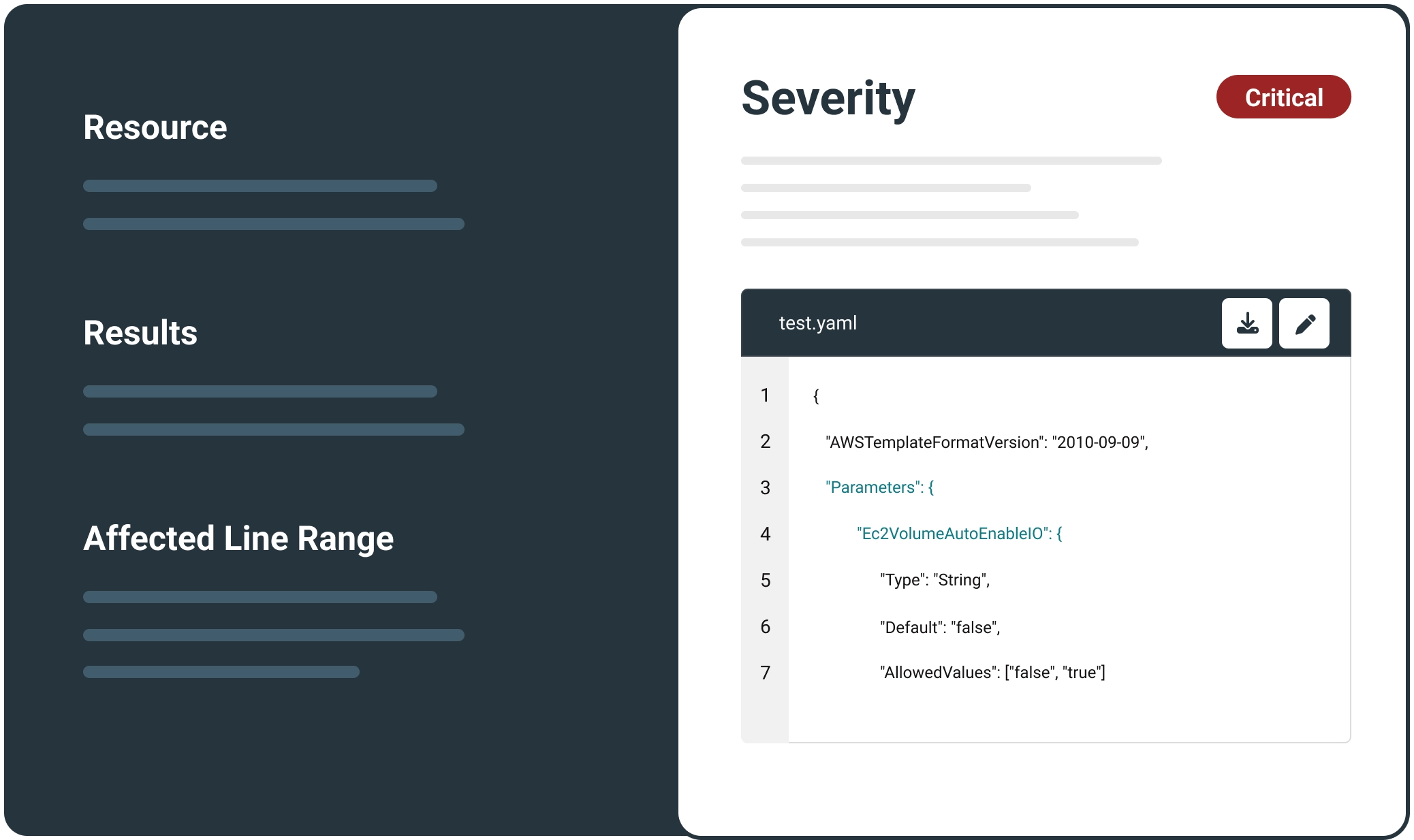
Enhance Your IaC Security with Carbonetes' BrainIAC
Effortlessly scan your IAC code for security misconfigurations and compliance issues. With hundreds of pre-defined rules and support for major platforms like Kubernetes, CloudFormation, Terraform, and more…
“
Infrastructure as Code (IaC) transforms IT management by enabling automation, consistency, and scalability. However, the frequent reuse of IaC makes it crucial to ensure security, as any misconfiguration can lead to widespread vulnerabilities. By integrating security into the IaC process, teams can identify and resolve issues early, reducing risks and avoiding costly fixes later. Empower your DevOps team now with Carbonetes BrainIAC.
Why IaC Security Matters
Not One Size Fits All
Much of security is implementing best practices. This is most evident in security policies with standard solutions like NIST and CIS. However, IaC doesn’t fit the “single standard” model because different applications and modules of applications will require different rights.
Best Practices
Your IaC tool, such as Carbonetes BrainIAC, should provide secure configuration recommendations, scan your code for deviations from best practices, and suggest improvements. It's then your decision to adjust based on the specific needs of your application.
Least Necessary Privilege
In an ideal world all deployments adhere to best practices, but sometimes apps require more privilege or flexibility. In these cases, you simply want to limit these deviations or “misconfigurations” are limited to those that are necessary for the specific application.
IaC Reuse
Developers and DevOps like to reuse code whenever possible for reasons of efficiency, stability and security. While reusing IaC is recommended, you need to ensure that the IaC you use adheres to principle of least necessary privilege. This means scanning each IaC to ensure your IaC is secure.
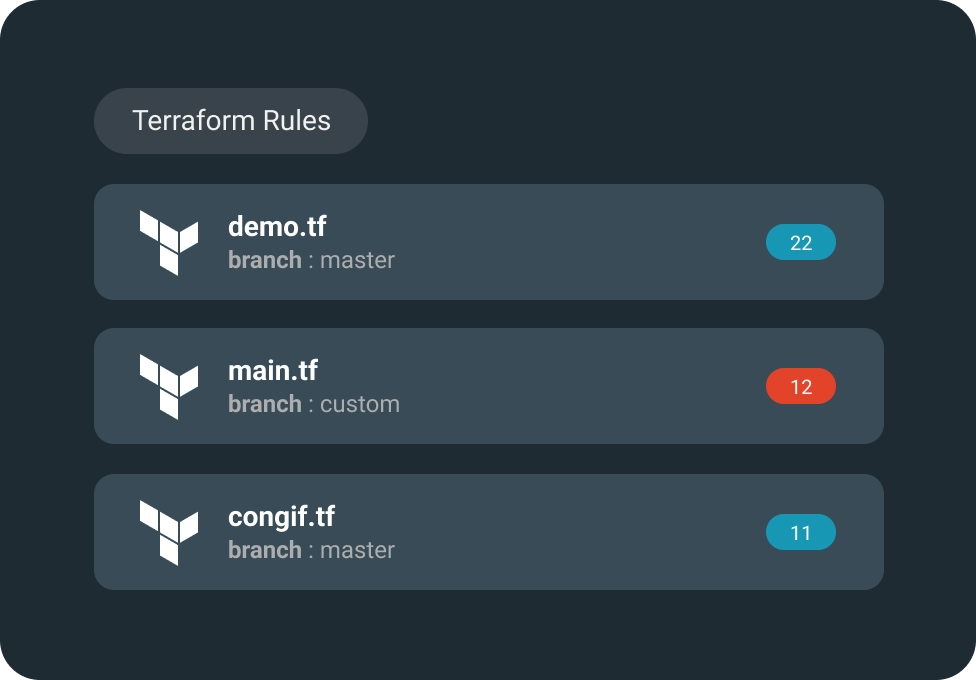
Platform/Service Considerations
Your IaC must address the rules of the platform you’ll deploy on. This includes containers, container orchestrators like Kuberenetes, cloud platforms, and cloud services.
Technical Features
One-Click In-Code Remediation
Carbonetes scans your IaC, offering in-line fix suggestions based on best practices. Apply or ignore with a single click for efficient remediation.
Developer-Centric Integrations
Secure IaC within developer workflows via IDEs, CLIs, SCMs, CI, Terraform Cloud, and enterprise integrations.
Optimized for Developer Adoption
BrainIAC integrates seamlessly with developer tools, minimizing disruption and encouraging the adoption of top security practices.
Industry’s Broadest Support
Carbonetes offers customizable security policies, built-in rulesets for Terraform, CloudFormation, ARM, Kubernetes and more. Backed by CIS benchmarks and best practices.
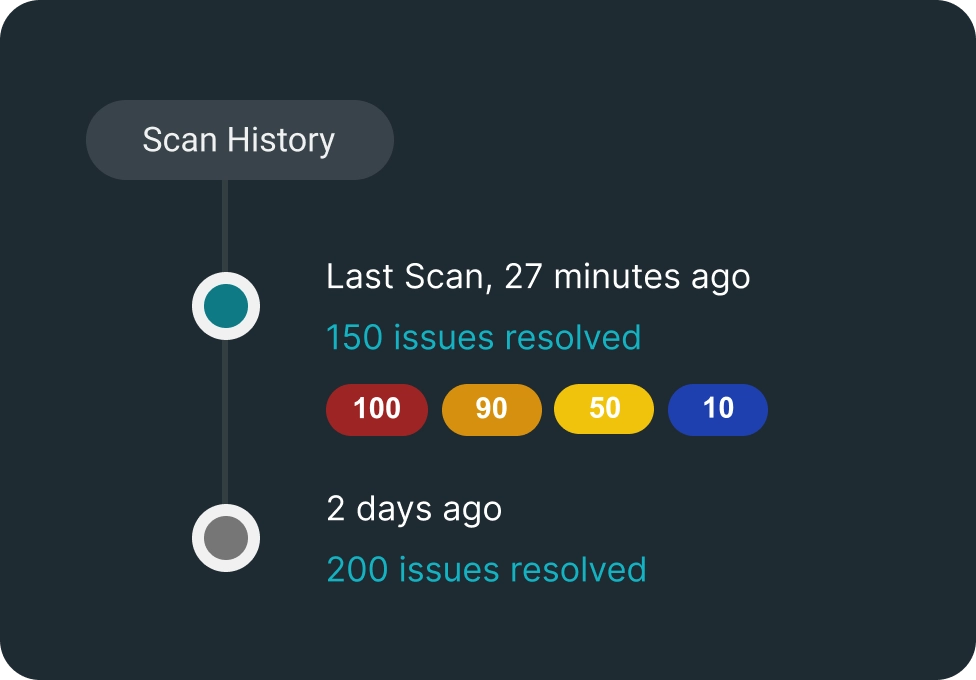
Issue Discovery
Carbonetes Enterprise provides an asset management tool for identifying misconfigurations, with BrainIAC generating reports that highlight issues, suggest fixes, offer insights.
Policy Compliance & Governance
Carbonetes policy tool identifies IaC misconfigurations that run afoul of the applicable policy and logs all activity for simplified governance
Benefits of Carbonetes' BrainIAC for IaC Security
Secure IaC with Minimal Effort
No Change to Your Workflows
Prevent Misconfigurations
Reduce Security Backlogs
Enforce Security Best Practices
“
Carbonetes’ automation dramatically reduces the time spent securing IaC code, enabling developers to focus on building new features.
“
Automated testing and gating of security issues within CI/CD pipelines ensures that your existing workflows are not changed, only secured.
“
Carbonetes BrainIAC ensures that your infrastructure is secure at every stage of the development and deployment lifecycle.
“
By empowering developers to identify and address security issues proactively, BrainIAC helps reduce security backlogs helping you complete your sprints on-time, while delivering the required security.
“
Policy tools in Lite and Enterprise ensure that you are alerted to potential misconfigurations so you can right size the privileges to the requirements of the application. You can easily track configuration issues over time and generate comprehensive reports on IaC security and compliance issues.
Secure your infrastructure as code configurations with Carbonetes' BrainIAC. Find and fix misconfigurations before they reach production and ensure robust protection for your applications and data.
Get Started with BrainIAC Today!
See BrainIAC in action and discover how our platform can transform your IaC security practices. Contact us now to schedule a live demo and take the first step towards a more secure development lifecycle.
Book a Live Demo Today!